Letsencrypt/certbot is great and it probably pays of using it in plenty of projects. There are some less known roadblock though that may slow you down.
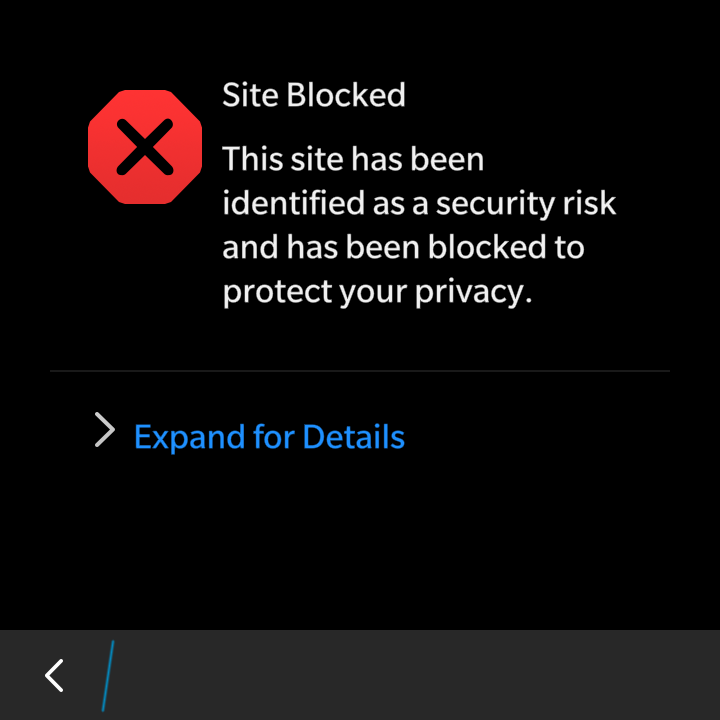
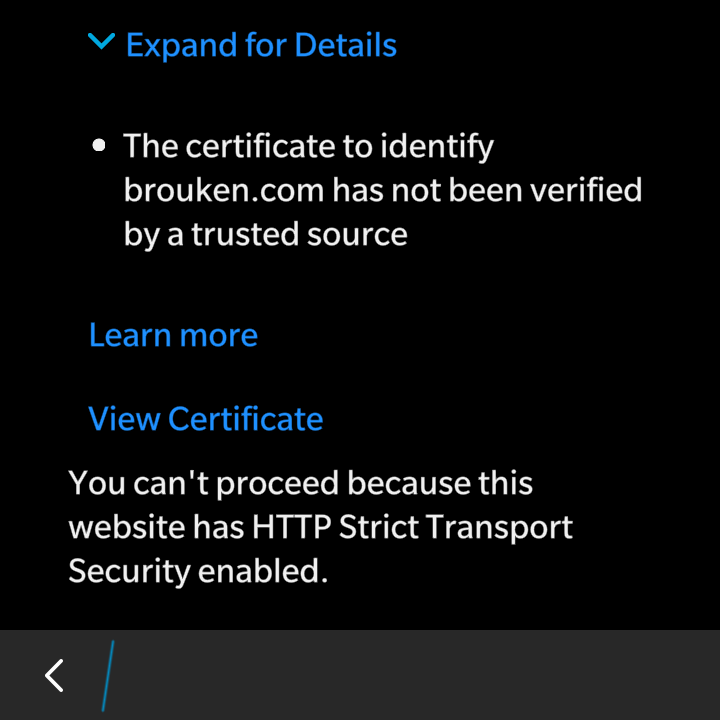
- IdenTrust isn’t known CA on BlackBerry OS 10 smartphones. For users that means confirming exception or importing the IdenTrust certificate to device’s root CA storage if site is using HSTS.
- Certbot doesn’t provide any service for automated certificate renewal. Most users end up using 3rd party cron scripts.
- There are some essential but less visible arguments (like –agree-tos or –email) for proper automated implementation of renewal tasks.
- Certbot features mandatory self-update mechanism that may prevent certificate renewal when self-update fails.
- The self-update mechanism includes compiling quite large python crypto libraries. This requires at least 300 to 400 MB of free RAM. That’s actually quite big issue for users of tiny VPS instances (some may be even without any swap). Is 1 GB RAM VPS enough? Maybe not (depending on currently running services).
- Certbot generates 4 files with different pem combinations. Thats ok for some web/mail servers but not for services such as ejabberd or lighttpd that need single file. That’s one more thing to cover…
- Services not running as root (ejabberd running on standard ports 52xx) are not able to read any certificate files because others have no read access to /etc/letsencrypt/live. Again, that’s additional case to take care of.